The Fundamental Technology Behind Cryptocurrencies: A Deep Dive
The fundamental technology behind cryptocurrencies, blockchain, is more than just a buzzword; it’s a revolutionary concept that has the potential to transform industries. This intricate web of interconnected blocks, each containing a record of transactions, forms a decentralized and secure ledger, offering a glimpse into a future where trust and transparency are paramount.
This technology, often hailed as the backbone of digital assets, empowers individuals and businesses alike, offering a new paradigm for financial interactions.
This article will delve into the intricacies of blockchain, exploring its core principles, cryptographic techniques, and consensus mechanisms. We’ll examine how these elements work together to create a robust and secure ecosystem for cryptocurrencies, fostering innovation and driving a new wave of technological advancement.
From the fundamental principles of cryptography to the intricacies of smart contracts, we’ll unravel the complexities of this groundbreaking technology, empowering you with a deeper understanding of the forces shaping the future of finance.
Blockchain Technology

Blockchain technology is the foundation upon which cryptocurrencies are built. It is a revolutionary distributed ledger system that enables secure, transparent, and efficient transactions without the need for intermediaries.
Understanding Blockchain
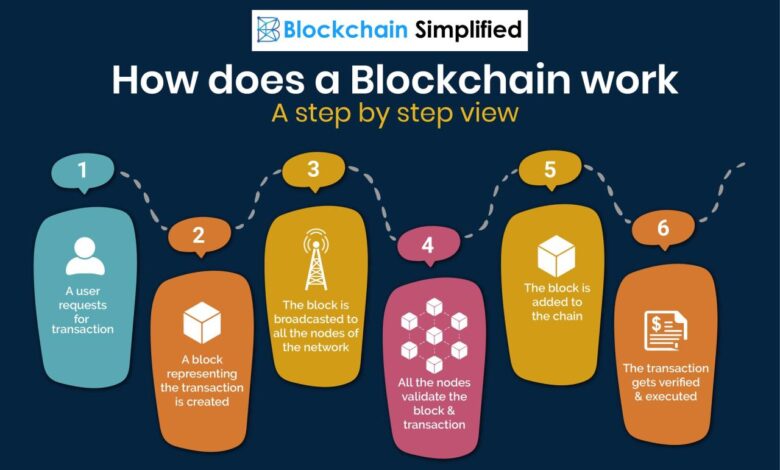
Blockchain is a chain of blocks, each containing a set of transactions. Each block is linked to the previous block through a cryptographic hash, creating a secure and immutable chain of data. This means that once a transaction is recorded on the blockchain, it cannot be altered or deleted.
Blockchain Security and Immutability
The security and immutability of blockchain transactions are ensured by several key features:* Cryptographic Hashing:Each block’s hash is calculated using a complex mathematical function, ensuring that any alteration to the block’s data will result in a different hash, making the alteration immediately detectable.
Decentralization
The blockchain is distributed across a network of computers, eliminating the risk of a single point of failure and making it resistant to tampering.
Consensus Mechanisms
Blockchain networks use consensus mechanisms, such as Proof-of-Work (PoW) or Proof-of-Stake (PoS), to ensure that all participants agree on the validity of transactions and the order of blocks in the chain.
Distributed Ledger Technology (DLT)
Blockchain is a specific type of DLT, which refers to a shared, immutable, and decentralized ledger that can record and verify transactions. DLTs can be used for various applications beyond cryptocurrencies, such as supply chain management, voting systems, and healthcare records.
Blockchain Consensus Mechanisms
Different blockchain networks employ various consensus mechanisms to validate transactions and maintain the integrity of the chain. Here are some examples:* Proof-of-Work (PoW):This mechanism requires miners to solve complex mathematical problems to add new blocks to the chain. The first miner to solve the problem receives a reward in the form of cryptocurrency.
Bitcoin uses PoW.
Proof-of-Stake (PoS)
This mechanism allows users to validate transactions by staking their cryptocurrency holdings. The more cryptocurrency a user stakes, the higher their chances of being selected to validate transactions. Ethereum 2.0 utilizes PoS.
Delegated Proof-of-Stake (DPoS)
This mechanism allows users to vote for “delegates” who are responsible for validating transactions. DPoS is used by EOS and Steem.
The blockchain, the fundamental technology behind cryptocurrencies, is a distributed ledger that records transactions in a secure and transparent manner. It’s fascinating how this technology has evolved, much like the way the food world has evolved and remembered the culinary genius of Diana Kennedy, a true icon of Mexican cuisine.
Both blockchain and Kennedy’s legacy represent innovation and a lasting impact on their respective fields.
Proof-of-Authority (PoA)
This mechanism relies on a small group of pre-selected validators who are trusted to maintain the integrity of the chain. PoA is used by networks that prioritize speed and efficiency.
“Blockchain is a revolutionary technology that has the potential to transform many industries. Its security, transparency, and efficiency make it a valuable tool for a wide range of applications.”
Cryptographic Techniques

Cryptographic techniques are the backbone of cryptocurrency systems, ensuring the security, integrity, and trust of transactions. They provide a robust foundation for managing and securing digital assets. These techniques are essential for protecting sensitive information, verifying the authenticity of transactions, and preventing unauthorized access to cryptocurrency wallets.
Hashing
Hashing is a cryptographic function that converts any data input, regardless of size, into a fixed-length string of characters called a hash. This hash is unique to the input data and serves as a digital fingerprint. Even a minor change in the input data will result in a completely different hash.
- One-way function:Hashing is a one-way function, meaning it is computationally infeasible to reverse the process and obtain the original data from the hash. This makes it impossible to forge transactions or alter data without detection.
- Collision resistance:Hashing algorithms are designed to be collision-resistant, meaning it is extremely difficult to find two different inputs that produce the same hash. This ensures the uniqueness and integrity of each transaction.
- Examples:Popular hashing algorithms used in cryptocurrency include SHA-256 (used by Bitcoin) and Keccak-256 (used by Ethereum).
Digital Signatures
Digital signatures are used to verify the authenticity and integrity of digital messages. They are created using a combination of hashing and asymmetric cryptography.
- Public-private key pair:Each user has a unique pair of keys: a public key and a private key. The public key can be shared with anyone, while the private key must be kept secret.
- Signing process:To sign a message, the sender uses their private key to encrypt the hash of the message. The resulting encrypted hash is the digital signature.
- Verification process:The recipient uses the sender’s public key to decrypt the digital signature and compare it to the hash of the message. If the hashes match, it confirms the message’s authenticity and integrity.
Encryption, The fundamental technology behind cryptocurrencies
Encryption is a process that transforms data into an unreadable format, known as ciphertext, making it inaccessible to unauthorized individuals.
The fundamental technology behind cryptocurrencies, blockchain, is a decentralized system that records transactions in a secure and transparent manner. This technology has the potential to revolutionize various industries, including finance, but it also faces challenges like scalability and regulation.
As Pelosi starts her Asia tour, China has warned of military action if she visits Taiwan, a situation that highlights the geopolitical tensions surrounding Taiwan. This event underscores the importance of secure and reliable technologies like blockchain, which can help to build trust and transparency in a world increasingly reliant on digital systems.
- Symmetric-key encryption:This type of encryption uses the same key for both encryption and decryption. It is generally faster than asymmetric encryption but requires secure key exchange.
- Asymmetric-key encryption:This type of encryption uses separate keys for encryption and decryption. It is more secure than symmetric encryption because it does not require the exchange of secret keys.
- Examples:Popular encryption algorithms used in cryptocurrency include AES (Advanced Encryption Standard) and RSA (Rivest-Shamir-Adleman).
Cryptographic Keys
Cryptographic keys are essential for managing and securing cryptocurrency assets. They are used to encrypt and decrypt data, sign transactions, and control access to wallets.
- Private keys:Private keys are secret and must be kept confidential. They are used to sign transactions and control access to cryptocurrency wallets.
- Public keys:Public keys can be shared with anyone. They are used to verify the authenticity of digital signatures and receive cryptocurrency transactions.
- Key management:Proper key management is crucial for securing cryptocurrency assets. It involves generating, storing, and using keys securely.
Comparison of Cryptographic Algorithms
Different cryptocurrency networks employ various cryptographic algorithms, each with its strengths and weaknesses.
- Hashing algorithms:SHA-256 (Bitcoin) and Keccak-256 (Ethereum) are widely used hashing algorithms known for their security and efficiency.
- Encryption algorithms:AES and RSA are commonly used for encryption, providing different levels of security and performance.
- Digital signature algorithms:ECDSA (Elliptic Curve Digital Signature Algorithm) is commonly used in cryptocurrency for its efficiency and security.
Consensus Mechanisms: The Fundamental Technology Behind Cryptocurrencies
In the realm of cryptocurrencies, consensus mechanisms are the backbone that ensures the integrity and security of the blockchain. They serve as the underlying rules and processes that govern how participants in a decentralized network reach agreement on the validity of transactions and the state of the blockchain.
Different Consensus Mechanisms
The following table Artikels some of the most prevalent consensus mechanisms used in cryptocurrency networks:
| Mechanism Name | Description | Advantages | Disadvantages |
|---|---|---|---|
| Proof of Work (PoW) | Miners compete to solve complex mathematical problems to validate transactions and add new blocks to the blockchain. The first miner to solve the problem receives a reward in the form of cryptocurrency. |
|
|
| Proof of Stake (PoS) | Instead of mining, validators are selected to validate transactions based on the amount of cryptocurrency they hold (their stake). They are rewarded for their participation and penalized for misconduct. |
|
|
| Delegated Proof of Stake (DPoS) | Users elect representatives (delegates) to validate transactions. Delegates are responsible for securing the network and are rewarded for their participation. |
|
|
| Proof of Authority (PoA) | Transactions are validated by a pre-selected set of trusted nodes. This mechanism is typically used in private or permissioned blockchains. |
|
|
Role of Consensus Mechanisms
Consensus mechanisms play a crucial role in validating transactions and maintaining the integrity of the blockchain. They ensure that:
- Transactions are verified and recorded accurately: Each transaction is checked for validity and consistency with the blockchain’s rules before being added to the ledger.
- The blockchain remains tamper-proof: Consensus mechanisms prevent malicious actors from altering the blockchain’s history or creating fraudulent transactions.
- The network operates in a decentralized and distributed manner: By relying on a distributed consensus, the network avoids a single point of failure and remains resistant to attacks.
Trade-offs of Different Consensus Mechanisms
Different consensus mechanisms offer varying trade-offs in terms of security, scalability, and energy consumption:
- Security: PoW is considered the most secure consensus mechanism due to its reliance on computational power. PoS and DPoS offer a balance between security and efficiency, while PoA prioritizes efficiency but may be less secure.
- Scalability: PoW can be slow and expensive to process transactions, while PoS, DPoS, and PoA offer higher scalability and faster transaction speeds. However, scalability can come at the cost of security.
- Energy Consumption: PoW is notoriously energy-intensive, while PoS and DPoS are significantly more energy-efficient. PoA consumes minimal energy but may be less secure.
Smart Contracts
Smart contracts are self-executing agreements written in code and stored on a blockchain. They automate the execution of terms and conditions, eliminating the need for intermediaries and ensuring transparency and immutability.
Smart Contract Applications
Smart contracts have revolutionized the way transactions are conducted in the cryptocurrency world. They enable a wide range of applications, including:
- Decentralized Finance (DeFi):Smart contracts power DeFi platforms, allowing users to lend, borrow, and trade cryptocurrencies without relying on traditional financial institutions. For example, a smart contract can automatically execute a loan agreement, ensuring that the borrower repays the loan on time with interest, while the lender receives their principal and interest payments.
The fundamental technology behind cryptocurrencies, blockchain, is all about decentralized security and transparency. It’s fascinating how this technology, designed for financial transactions, is now being used to track and secure data in other sectors, like the military. For example, the pentagon planning for possible pelosi trip to taiwan ap has sparked a lot of discussion about how blockchain could be used to secure sensitive information and communication in a volatile geopolitical situation.
The future of blockchain is certainly looking bright, with its applications expanding beyond finance and into areas we might not have even imagined.
- Non-Fungible Tokens (NFTs):Smart contracts are essential for creating and managing NFTs, which represent unique digital assets. A smart contract can define the ownership, transferability, and other characteristics of an NFT, ensuring its authenticity and provenance.
- Supply Chain Management:Smart contracts can track the movement of goods along a supply chain, providing real-time visibility and transparency. For instance, a smart contract can record the origin, transportation, and delivery of products, preventing counterfeiting and ensuring product quality.
- Decentralized Autonomous Organizations (DAOs):Smart contracts form the foundation of DAOs, allowing members to vote on proposals, manage funds, and execute decisions in a transparent and decentralized manner. For example, a DAO could use a smart contract to distribute funds to members based on their contributions or to manage the development of a project.
Benefits of Smart Contracts
Smart contracts offer several advantages over traditional contracts, including:
- Automation:Smart contracts eliminate the need for manual intervention, ensuring that transactions are executed automatically and efficiently.
- Transparency:All smart contract code and transactions are publicly visible on the blockchain, promoting trust and accountability.
- Immutability:Once deployed, smart contracts cannot be altered, preventing fraud and manipulation.
- Security:Smart contracts are secure and tamper-proof due to the cryptographic nature of the blockchain.
- Efficiency:Smart contracts reduce the time and cost associated with traditional contracts, streamlining business processes.
Limitations of Smart Contracts
Despite their numerous benefits, smart contracts also have limitations:
- Security vulnerabilities:While smart contracts are generally secure, they can be susceptible to vulnerabilities if not properly designed and audited.
- Limited functionality:Smart contracts are currently limited in their ability to interact with the real world, such as accessing data from external sources or controlling physical devices.
- Lack of legal recognition:The legal status of smart contracts is still evolving, and there is no universal legal framework for their enforcement.
- Difficulty of auditing:Auditing smart contracts can be complex and time-consuming, requiring specialized expertise.
Smart Contract Languages
Various programming languages are used to develop smart contracts, each with its own features and capabilities.
| Language | Features |
|---|---|
| Solidity | Developed by Ethereum, widely used for smart contracts on the Ethereum blockchain. Object-oriented, supports inheritance, and allows for complex logic. |
| Vyper | A Python-inspired language designed for security and simplicity. Emphasizes safety and clarity, making it suitable for critical applications. |
| Rust | A systems programming language known for its memory safety and performance. Gaining popularity for smart contract development due to its robust features. |
| AssemblyScript | A TypeScript-based language that compiles to WebAssembly, offering high performance and compatibility with existing JavaScript tools. |
Mining and Validation
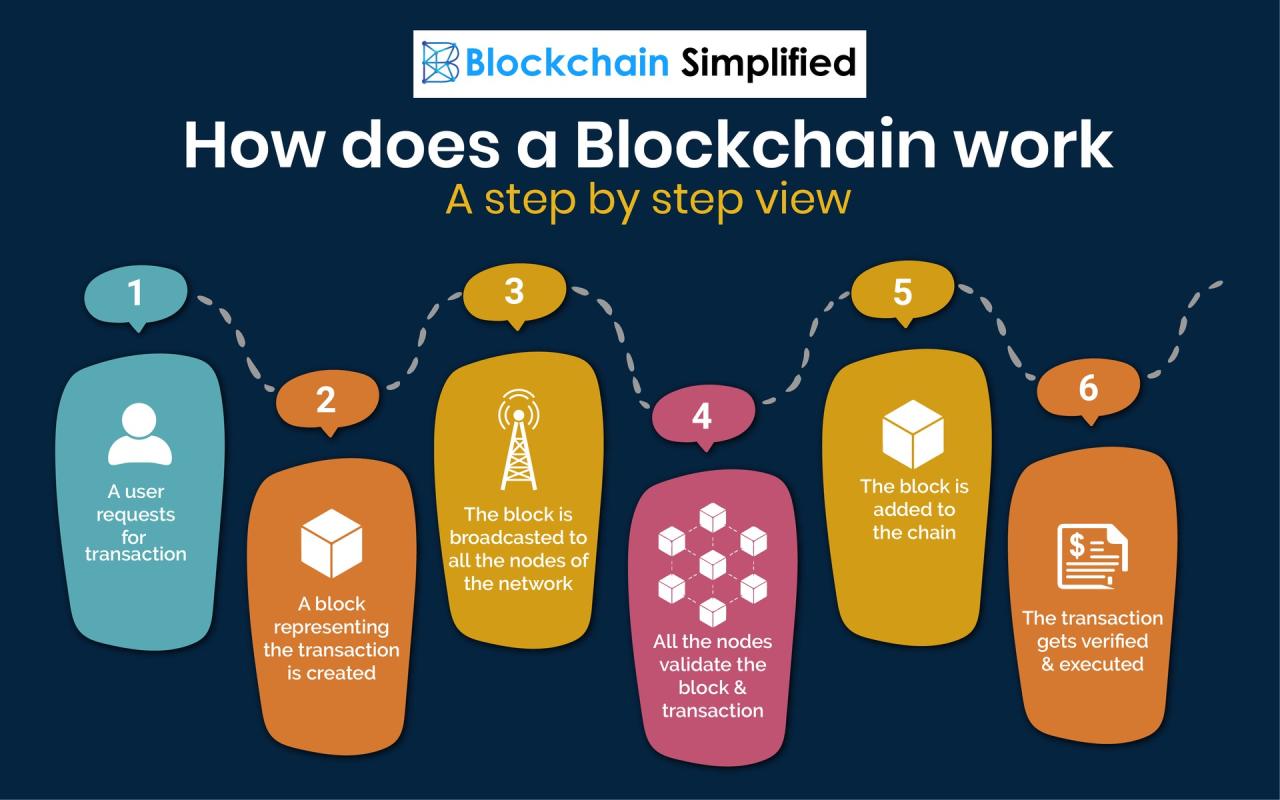
Cryptocurrency mining is the process by which transactions are verified and added to the blockchain, a public ledger that records all transactions. This process is crucial for maintaining the security and integrity of the blockchain network. Miners use specialized hardware to solve complex mathematical problems, and the first miner to solve the problem receives a reward in the form of cryptocurrency.
This process is known as Proof-of-Work (PoW).
Mining Hardware
The type of hardware used for mining depends on the specific cryptocurrency and the level of complexity involved in the mining process. Here are some common types of mining hardware:
- Central Processing Units (CPUs):While CPUs are typically used for general computing tasks, they can also be used for mining, especially for less complex cryptocurrencies. However, their efficiency is limited compared to specialized hardware.
- Graphics Processing Units (GPUs):GPUs are designed for parallel processing, making them ideal for solving the complex mathematical problems involved in mining. They offer significantly better performance than CPUs for mining.
- Application-Specific Integrated Circuits (ASICs):ASICs are specialized hardware designed specifically for cryptocurrency mining. They offer the highest level of performance and efficiency, making them the preferred choice for large-scale mining operations.
Economic Incentives and Challenges
Cryptocurrency mining offers significant economic incentives, including:
- Block Rewards:Miners receive block rewards for successfully verifying and adding transactions to the blockchain. These rewards are typically paid in the cryptocurrency being mined.
- Transaction Fees:Some cryptocurrencies allow users to pay transaction fees, which are distributed to miners. These fees incentivize miners to process transactions quickly and efficiently.
However, cryptocurrency mining also presents several challenges:
- High Energy Consumption:Mining requires significant computational power, which translates to high energy consumption. This can be a major cost factor for miners, especially with rising electricity prices.
- Competition:The mining landscape is highly competitive, with a constant race to acquire the most powerful hardware and optimize mining operations. This makes it challenging for new miners to enter the market and be profitable.
- Volatility:The value of cryptocurrencies can fluctuate significantly, impacting the profitability of mining operations. A sudden drop in the price of a cryptocurrency can make mining unprofitable.
Block Rewards and Cryptocurrency Supply
Block rewards are a crucial element of the cryptocurrency ecosystem. They incentivize miners to secure the blockchain network and contribute to the validation of transactions. Each time a new block is added to the blockchain, the miners who successfully solve the cryptographic puzzle receive a block reward.
This reward is typically a fixed amount of the cryptocurrency being mined.The block reward mechanism plays a significant role in controlling the cryptocurrency supply. For example, Bitcoin’s block reward is halved every four years. This halving mechanism ensures that the supply of Bitcoin remains limited, preventing inflation and maintaining its value.
The halving mechanism is a key feature of Bitcoin’s design, aiming to create a deflationary model where the supply of Bitcoin is limited, similar to gold.
The block reward mechanism is a complex and dynamic aspect of cryptocurrency mining. It impacts the profitability of mining operations, the supply of cryptocurrencies, and the overall security of the blockchain network.
End of Discussion
Understanding the fundamental technology behind cryptocurrencies is essential for navigating this evolving landscape. From the robust security of blockchain to the transformative potential of smart contracts, this technology is redefining the way we interact with financial systems. As we delve deeper into the intricacies of this revolutionary technology, we gain a clearer picture of its potential to revolutionize industries, empower individuals, and shape a more transparent and secure future.