Cybersecurity
-

Cybersecurity Challenges of the Hybrid Workplace: Tackling the Risks
Cybersecurity challenges of the hybrid workplace and how to tackle them – The rise of the hybrid workplace, with its…
Read More » -

Cybersecurity Insurance: Get Coverage, Save Money
How to get cybersecurity insurance and keep costs as low as possible? It’s a question on every business owner’s mind,…
Read More » -

How Not to Become the Victim of Online Fraud
How not to become the victim of online fraud is a question that’s becoming increasingly important in our digital age.…
Read More » -

How to Address Cyber Threats Against Higher Ed: A Comprehensive Guide
How to address cyber threats against higher ed sets the stage for this enthralling narrative, offering readers a glimpse into…
Read More » -

MHA Body Issues Norms for Crypto Crimes
Mha body issues norms for crypto related crimes – MHA Body Issues Norms for Crypto Crimes takes center stage as…
Read More » -

Home Business Entrepreneurs: 6 Ways to Prevent Data Breaches
Home business entrepreneurs the 6 best ways to prevent data breaches – Home business entrepreneurs: the 6 best ways to…
Read More » -
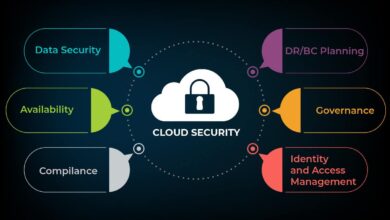
Cloud Security Scaling: Protecting Large, Multi-Site Campuses
How cloud based technology can scale security for large and multi site campuses – How cloud-based technology can scale security…
Read More » -
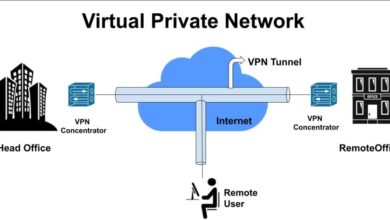
What Is Remote Access VPN and How Does It Work?
What is remote access vpn how does it work – What is remote access VPN and how does it work?…
Read More »



