What is Remote Access VPN and How Does It Work?
What is remote access vpn how does it work – What is remote access VPN and how does it work? These are questions many people ask when they hear about this technology, which has become increasingly crucial in our increasingly digital world. A remote access VPN essentially creates a secure tunnel between your device and a remote network, allowing you to access resources as if you were physically connected.
Imagine you’re at home, but you need to access files on your work computer. A remote access VPN allows you to do just that, securely and privately, as if you were sitting in the office.
Think of it like a secret passageway. Instead of sending your data through the open internet, a remote access VPN encrypts it and sends it through a secure tunnel, making it difficult for anyone to intercept or see your information.
This encryption process is vital for protecting sensitive data, like financial information or personal files, from unauthorized access. It also allows you to access geographically restricted content, like streaming services, from anywhere in the world.
What is a VPN?
A Virtual Private Network (VPN) is a technology that creates a secure and encrypted connection between your device and the internet. It acts as a tunnel, protecting your online activity from prying eyes and ensuring your data remains private.
Purpose of VPNs
VPNs are primarily used to enhance online security and privacy. They achieve this by:
- Encrypting your internet traffic:All data sent and received through a VPN is encrypted, making it unreadable to anyone who intercepts it. This is like putting your data in a locked box that only you and the recipient have the key to open.
- Masking your IP address:A VPN hides your real IP address, replacing it with one from the VPN server’s location. This prevents websites and online services from tracking your location and browsing activity.
- Bypassing geo-restrictions:Some websites and services restrict content based on your location. A VPN allows you to access content from other countries by connecting to a server in that region.
How VPNs Work
Imagine you want to send a letter to a friend in another city. Instead of sending it directly through the mail, you decide to use a secure courier service. The courier picks up your letter, puts it in a locked box, and delivers it to your friend.
A VPN works similarly. When you connect to a VPN, your internet traffic is routed through a VPN server. This server acts as the courier, encrypting your data and sending it to its destination. The VPN server then decrypts the data and delivers it to the intended recipient.
This entire process ensures your data remains secure and private throughout its journey.
Remote Access VPN: What Is Remote Access Vpn How Does It Work
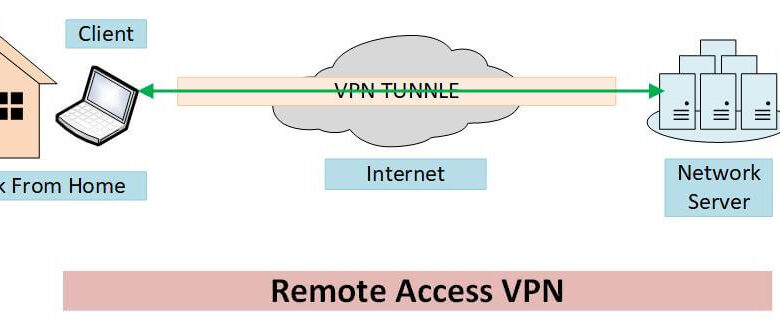
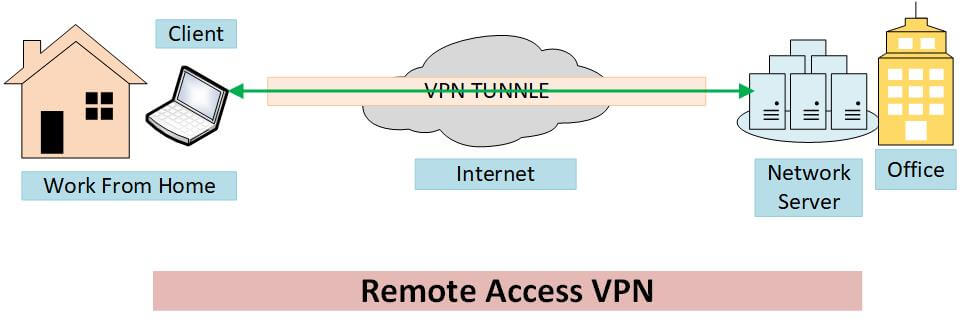
A remote access VPN is a type of VPN that allows users to securely connect to a private network from a remote location, such as their home or a public Wi-Fi network. This type of VPN is often used by employees who need to access company resources, such as email, files, and applications, from outside the office.Remote access VPNs are a crucial tool for businesses and individuals seeking secure and private access to networks and resources.
They establish a secure tunnel between a user’s device and the network, encrypting all data transmitted through the tunnel. This encryption ensures that sensitive information is protected from unauthorized access and eavesdropping.
How Remote Access VPNs Enable Secure Access
Remote access VPNs enable secure access to private networks by establishing a secure connection between the user’s device and the network. This connection is typically established using a VPN client, which is a software application that runs on the user’s device.
The VPN client connects to a VPN server, which is a dedicated server that resides on the private network.Once the connection is established, all data transmitted between the user’s device and the private network is encrypted and sent through the secure tunnel created by the VPN.
This encryption ensures that the data is protected from unauthorized access and eavesdropping.
Examples of Remote Access VPN Usage
Remote access VPNs are used in a variety of scenarios, including:
- Employees working from home or on the road who need to access company resources.
- Freelancers or contractors who need to access client networks.
- Students who need to access university resources from off-campus.
- Individuals who want to access streaming services that are not available in their region.
- Users who want to protect their online privacy and security when using public Wi-Fi networks.
How Remote Access VPNs Work
Remote access VPNs establish secure connections between your device and a remote server, allowing you to access resources as if you were physically connected to the network. This process involves several steps, leveraging encryption and VPN protocols to ensure secure data transmission.
Encryption
Encryption plays a crucial role in securing data transmitted through a VPN. Data is scrambled into an unreadable format before being sent over the network. The VPN server uses a unique key to decrypt the data upon arrival, making it accessible only to authorized users.
This encryption process protects your data from unauthorized access, even if someone intercepts the transmission.
Encryption is the process of converting information into a format that is unreadable without a decryption key.
VPN Protocols
VPN protocols define the methods used to establish and maintain secure connections. Some common protocols include:
- PPTP (Point-to-Point Tunneling Protocol): PPTP is one of the oldest VPN protocols, offering relatively simple setup but with weaker security compared to newer protocols.
- L2TP (Layer 2 Tunneling Protocol): L2TP provides a more secure connection than PPTP, often used in conjunction with IPSec encryption.
- OpenVPN: OpenVPN is considered one of the most secure VPN protocols, utilizing strong encryption algorithms and a robust open-source implementation.
Components of a Remote Access VPN
A remote access VPN system is comprised of several key components that work together to establish a secure connection between a remote user and a private network. These components facilitate secure communication and ensure data privacy during remote access.
VPN Clients
The VPN client is the software installed on the remote user’s device, which acts as the entry point for the secure connection. It establishes a connection with the VPN server and encrypts all data transmitted between the user’s device and the VPN server.
The VPN client is responsible for:
- Establishing and maintaining a secure connection to the VPN server.
- Encrypting and decrypting data transmitted over the VPN tunnel.
- Managing user authentication and authorization.
- Providing a user interface for managing VPN connections.
VPN Servers
The VPN server is the central component of the remote access VPN system. It receives connection requests from VPN clients, authenticates users, and establishes secure tunnels to allow access to the private network. The VPN server is responsible for:
- Handling connection requests from VPN clients.
- Authenticating users and granting access to the private network.
- Managing encryption and decryption of data transmitted through the VPN tunnel.
- Routing traffic to the appropriate destination within the private network.
VPN Gateways
The VPN gateway acts as a bridge between the public internet and the private network. It receives encrypted data from the VPN server and forwards it to the appropriate destination within the private network. The VPN gateway plays a crucial role in:
- Routing encrypted traffic between the VPN server and the private network.
- Enforcing security policies and access controls for the private network.
- Monitoring and logging VPN traffic for security and auditing purposes.
VPN Tunnels
A VPN tunnel is a secure, encrypted connection established between the VPN client and the VPN server. It acts as a virtual pipe that encapsulates all data transmitted between the two endpoints, ensuring data confidentiality and integrity. The VPN tunnel is responsible for:
- Providing a secure and encrypted communication channel between the VPN client and the VPN server.
- Protecting data from unauthorized access and interception during transmission.
- Enhancing data integrity by verifying the authenticity of the data received.
Benefits of Using a Remote Access VPN
Remote access VPNs offer a range of benefits for individuals and businesses, enhancing security, privacy, and accessibility. These benefits extend to various aspects of digital life, from personal browsing and online transactions to remote work and business operations.
Remote access VPNs are like secure tunnels that let you access your work computer from anywhere, encrypting your data to keep it safe. While we’re on the topic of security and access, it’s interesting to consider the recent call for action, “Will the pro-abortion rights billionaires please stand up,” a question demanding action on a critical social issue.
Back to VPNs, these virtual private networks can also help you bypass geo-restrictions, giving you access to websites and content that might otherwise be blocked.
Security Benefits
Remote access VPNs provide robust security features that protect your data and privacy while you’re online. Here’s how:
- Data Encryption:VPNs encrypt your internet traffic, transforming it into an unreadable code. This makes it virtually impossible for unauthorized individuals or entities to intercept and decipher your data, safeguarding sensitive information like passwords, financial details, and personal communications.
- IP Address Masking:VPNs mask your actual IP address, replacing it with one from their server network. This makes it difficult to track your online activities, protecting your privacy and making it harder for websites and advertisers to target you with personalized ads.
- Protection from Public Wi-Fi:When you connect to public Wi-Fi networks, your data is vulnerable to eavesdropping and potential attacks. VPNs create a secure tunnel between your device and the VPN server, shielding your traffic from prying eyes and enhancing your security in public settings.
Remote access VPNs are like secure tunnels that let you access your work computer from anywhere. They encrypt your data, making it impossible for hackers to snoop. This kind of security is essential for entrepreneurs who need to stay connected and productive no matter where they are.
And speaking of productivity, check out this article on 11 mindset traits of successful entrepreneurs to see how they stay ahead of the game. Just like a VPN, a strong mindset is key to navigating the challenges of entrepreneurship.
Remote access VPNs are a powerful tool for entrepreneurs, offering a safe and reliable way to stay connected to their business from any location.
Privacy Benefits
Remote access VPNs play a crucial role in safeguarding your online privacy by:
- Preventing Tracking:VPNs prevent websites and advertisers from tracking your online activities, browsing history, and location. This helps maintain your anonymity and limits the collection of personal data for targeted advertising and profiling.
- Circumventing Geo-restrictions:VPNs allow you to access content that is restricted based on your location. By connecting to a server in a different country, you can bypass geo-blocks and access streaming services, websites, and online content that might be unavailable in your region.
Remote Access and Remote Work Capabilities
Remote access VPNs enable secure and reliable remote access to networks, resources, and applications, facilitating remote work and business operations:
- Secure Remote Access:VPNs provide a secure and encrypted connection for remote employees to access company networks, files, and applications. This allows them to work remotely with the same level of security as if they were in the office.
- Enhanced Collaboration:VPNs enable seamless collaboration among remote teams by providing a secure and reliable platform for sharing files, accessing shared resources, and conducting virtual meetings. This facilitates efficient communication and teamwork, regardless of physical location.
- Increased Flexibility and Productivity:Remote access VPNs empower employees to work from anywhere with an internet connection, increasing flexibility and productivity. They can access company resources and collaborate with colleagues without being physically present in the office.
Setting Up and Using a Remote Access VPN
Setting up and using a remote access VPN is a straightforward process, involving a few simple steps. The first step is to choose a reliable VPN provider, then create an account, and download the VPN client software for your devices.
After that, you can easily connect to the VPN server and start enjoying its benefits.
Setting Up a VPN Connection
The process of setting up a VPN connection involves a few steps, which are generally similar across different VPN providers.
- Choose a VPN provider: There are many VPN providers available, each with its own features, pricing, and security protocols. It is important to research and choose a reputable VPN provider that meets your specific needs. Look for providers that offer strong encryption, a wide server network, a no-logs policy, and excellent customer support.
Consider factors like speed, reliability, and ease of use when making your decision.
- Create an account: Once you have chosen a VPN provider, you will need to create an account. This typically involves providing your email address, password, and payment information. Some providers offer free trials or limited free plans to allow you to test their service before committing to a paid subscription.
- Download the VPN client: After creating an account, you will need to download the VPN client software for your devices. Most VPN providers offer clients for Windows, macOS, iOS, Android, and other popular platforms. The VPN client software will allow you to connect to the VPN server and establish a secure connection.
- Install and configure the VPN client: Once you have downloaded the VPN client, you will need to install it on your devices. The installation process is usually straightforward and involves following the on-screen instructions. After installing the VPN client, you will need to configure it by entering your account credentials and selecting a VPN server.
Some VPN clients may require you to configure additional settings, such as the encryption protocol or the type of connection.
- Connect to the VPN server: Once the VPN client is installed and configured, you can connect to the VPN server. This usually involves clicking a connect button within the VPN client software. The VPN client will then establish a secure connection to the VPN server, encrypting your internet traffic and routing it through the VPN server.
Remote access VPNs create a secure connection between your device and a remote server, encrypting all your data and making it appear as if you’re browsing from the server’s location. It’s a powerful tool for privacy and security, but sometimes even with all the protection in the world, we’re reminded of the harsh realities, like the tragic story of the Columbia graduate student brutally beaten in Manhattan, leaving his mother searching for answers.
It’s a reminder that while technology can help us stay safe online, it can’t always shield us from the dangers of the physical world. Back to VPNs, they work by creating a secure tunnel through which all your data travels, making it virtually impossible for anyone to intercept or snoop on your activity.
You can then access the internet through the VPN server, enjoying the benefits of enhanced privacy, security, and anonymity.
Configuring VPN Clients on Different Devices
Configuring VPN clients on different devices can vary depending on the VPN provider and the operating system. However, the basic steps are generally similar.
- Windows: On Windows devices, you can configure VPN clients by going to the Network and Sharing Center, clicking on “Set up a new connection or network,” and selecting “Connect to a workplace.” You will then need to enter the VPN server address, your account credentials, and other relevant settings.
Some VPN providers offer dedicated Windows apps that simplify the configuration process.
- macOS: On macOS devices, you can configure VPN clients by going to System Preferences, clicking on “Network,” and then clicking on the “+” button to add a new VPN connection. You will then need to select the VPN type, enter the VPN server address, your account credentials, and other relevant settings.
Similar to Windows, some VPN providers offer dedicated macOS apps for easier configuration.
- iOS: On iOS devices, you can configure VPN clients by going to Settings, clicking on “VPN,” and then tapping on “Add VPN Configuration.” You will then need to select the VPN type, enter the VPN server address, your account credentials, and other relevant settings.
Many VPN providers offer dedicated iOS apps that simplify the configuration process and provide a user-friendly interface.
- Android: On Android devices, you can configure VPN clients by going to Settings, clicking on “Network & internet,” and then tapping on “VPN.” You will then need to select “Add VPN” and enter the VPN server address, your account credentials, and other relevant settings.
Many VPN providers offer dedicated Android apps that simplify the configuration process and provide a user-friendly interface.
Choosing a Reliable VPN Service Provider
Choosing a reliable VPN service provider is crucial for ensuring the security and privacy of your online activities. Here are some key factors to consider:
- Encryption: A strong encryption protocol, such as AES-256, is essential for protecting your data from unauthorized access. Look for VPN providers that use industry-standard encryption algorithms.
- Server network: A wide server network with servers in multiple locations allows you to choose the best server for your needs, ensuring fast speeds and reliable connections. Consider providers with servers in locations that are relevant to your online activities.
- No-logs policy: A no-logs policy means that the VPN provider does not track or store your browsing activity or other data. This is important for protecting your privacy and ensuring that your online activities remain anonymous.
- Customer support: Reliable customer support is essential for resolving any issues you may encounter with the VPN service. Look for providers that offer 24/7 support through multiple channels, such as email, live chat, or phone.
- Speed: The speed of a VPN connection can vary depending on the VPN provider, the server location, and the overall network conditions. Look for providers that offer fast speeds and reliable connections.
- Pricing: VPN providers offer different pricing plans, ranging from free to premium. Consider your budget and the features you need when choosing a VPN provider.
Remote Access VPN Security Considerations
While VPNs offer a significant layer of security for remote access, it’s crucial to understand that they are not foolproof. Several security risks and considerations must be addressed to ensure the effectiveness and safety of your VPN connection.
Choosing a Reputable VPN Provider
Selecting a reliable VPN provider is paramount for maintaining secure connections. Reputable VPN providers prioritize user privacy and security, employing strong encryption protocols, robust security measures, and transparent practices.
- Strong Encryption Protocols:Look for VPN providers that use industry-standard encryption protocols like AES-256, which are considered highly secure and difficult to crack.
- No-Logs Policy:Choose a provider that adheres to a strict no-logs policy, meaning they don’t store any data about your browsing activity or connection details.
- Independent Audits:Look for providers that undergo independent security audits to ensure their claims of security and privacy are verified by third-party experts.
- Location and Jurisdiction:Consider the provider’s location and jurisdiction, as it can influence data retention laws and potential government surveillance.
- Customer Support:A responsive and helpful customer support team is essential, especially if you encounter any technical issues or have security concerns.
Maintaining Secure VPN Connections
Beyond choosing a trustworthy provider, several additional steps can further enhance your VPN security:
- Use a Strong Password:Always use a unique and complex password for your VPN account, and avoid using the same password for multiple accounts.
- Enable Two-Factor Authentication (2FA):2FA adds an extra layer of security by requiring a second verification step, typically a code sent to your phone, before logging in.
- Keep Your VPN Software Updated:Regularly update your VPN software to benefit from the latest security patches and bug fixes.
- Avoid Public Wi-Fi:While VPNs can help secure your connection on public Wi-Fi, it’s still advisable to avoid sensitive tasks like online banking or shopping on unsecured networks.
- Be Cautious of Free VPNs:Free VPNs may offer limited features or compromise your privacy by selling your data to third parties. Consider opting for a paid VPN service for better security and reliability.
Potential Security Risks Associated with VPNs
Despite their benefits, VPNs are not immune to security risks. Understanding these risks can help you take proactive measures to mitigate them.
- Data Breaches:While rare, VPN providers can experience data breaches, potentially exposing your connection details or browsing history.
- Malware and Phishing:Malicious actors may try to exploit vulnerabilities in VPN software or trick users into downloading malware disguised as legitimate VPN apps.
- VPN Provider Compromise:In some cases, VPN providers may be compromised by government agencies or hackers, potentially allowing them to monitor your traffic or access your data.
- VPN Server Overloads:If a VPN server becomes overloaded, it can slow down your connection speed and potentially expose your traffic to other users on the same server.
- Misconfigured VPN Settings:Incorrectly configured VPN settings can create vulnerabilities that could expose your data or compromise your security.
Real-World Applications of Remote Access VPNs
Remote access VPNs are not just theoretical concepts; they are widely used across various industries and scenarios to enhance security, productivity, and accessibility. Let’s explore some real-world applications where remote access VPNs play a crucial role.
Industries Relying on Remote Access VPNs
Remote access VPNs are essential for businesses in various industries, enabling secure access to critical data and resources.
- Finance:Financial institutions rely heavily on VPNs to secure sensitive customer data, transactions, and internal systems. Remote access VPNs enable employees to access financial applications and databases from anywhere, ensuring data integrity and regulatory compliance.
- Healthcare:Hospitals and healthcare providers utilize VPNs to safeguard patient records, medical imaging, and other confidential information. Remote access VPNs allow doctors, nurses, and other healthcare professionals to securely access patient data from their homes or while traveling.
- Education:Educational institutions use VPNs to protect student records, academic research data, and administrative systems. Remote access VPNs enable faculty and staff to work remotely, access online resources, and conduct research securely.
- Government:Government agencies use VPNs to protect sensitive information, classified documents, and critical infrastructure. Remote access VPNs allow government employees to access confidential data from remote locations while ensuring data security.
- Technology:Technology companies heavily rely on VPNs to secure internal networks, manage code repositories, and provide remote access to developers and engineers. Remote access VPNs enable collaboration and development work from anywhere in the world.
Benefits of Using VPNs for Teleworking and Remote Access to Corporate Networks
The rise of remote work has significantly increased the demand for secure remote access solutions. Remote access VPNs offer numerous benefits for teleworking and accessing corporate networks remotely:
- Enhanced Security:VPNs encrypt all data transmitted between the user’s device and the corporate network, preventing unauthorized access and data breaches. This is especially crucial for employees working from home or public Wi-Fi networks.
- Improved Productivity:VPNs enable employees to access corporate resources and applications from anywhere, allowing them to work remotely without compromising productivity. This flexibility can enhance employee satisfaction and reduce commute times.
- Cost Savings:Implementing a VPN can reduce the need for physical office space and associated costs, such as rent, utilities, and maintenance. This can significantly impact a company’s bottom line, especially for businesses with a geographically dispersed workforce.
- Compliance and Regulations:Many industries have strict data security and compliance regulations. VPNs can help businesses meet these regulations by ensuring secure data transmission and access control. This is particularly important for industries like healthcare, finance, and government.
- Scalability and Flexibility:VPNs are highly scalable and flexible, allowing businesses to easily add or remove users as needed. This makes them ideal for businesses with rapidly changing workforce dynamics or seasonal fluctuations.
Remote Access VPN vs. Other Technologies
Remote access VPNs are not the only way to access resources remotely. Other technologies like SSH and RDP offer similar functionalities. Understanding the differences between these technologies is crucial for choosing the best solution for your specific needs. This section compares and contrasts remote access VPNs with SSH and RDP, highlighting their advantages, disadvantages, and ideal use cases.
Comparison of Remote Access VPN, SSH, and RDP
Remote access VPNs, SSH, and RDP are all technologies that allow remote access to computer systems. However, they differ in their underlying mechanisms, security features, and intended use cases.
- Remote Access VPN: Remote access VPNs create a secure tunnel between your device and a remote network. This tunnel encrypts all data transmitted between the two points, making it secure from eavesdropping. Remote access VPNs are typically used for accessing company resources, accessing the internet securely, and bypassing geo-restrictions.
- SSH (Secure Shell): SSH is a protocol used for secure remote access to a server. It provides a secure connection for managing and running commands on the server. SSH is often used for managing servers, deploying software, and running scripts.
- RDP (Remote Desktop Protocol): RDP is a protocol used for remote access to a graphical desktop environment. It allows you to control a remote computer as if you were sitting in front of it. RDP is commonly used for remote administration, remote work, and accessing applications on a remote computer.
Advantages and Disadvantages, What is remote access vpn how does it work
Each technology has its own advantages and disadvantages:
| Technology | Advantages | Disadvantages |
|---|---|---|
| Remote Access VPN |
|
|
| SSH |
|
|
| RDP |
|
|
Ideal Use Cases
The choice of technology depends on the specific use case. Here are some scenarios where each technology is most appropriate:
- Remote Access VPN: Ideal for accessing company resources, securing internet connections, and bypassing geo-restrictions.
- SSH: Best for managing servers, deploying software, and running scripts.
- RDP: Suitable for remote administration, remote work, and accessing applications on a remote computer.
Future Trends in Remote Access VPNs
The landscape of remote access VPNs is constantly evolving, driven by advancements in technology, changing user needs, and the growing adoption of remote work. As we move forward, we can expect to see a number of exciting trends shaping the future of VPNs.
Emerging VPN Protocols
The development of new VPN protocols is a key area of innovation. Existing protocols, such as OpenVPN and WireGuard, are constantly being improved, while new protocols are emerging, each with its own strengths and weaknesses.
- WireGuard:This protocol is known for its simplicity, speed, and security. It is becoming increasingly popular for its lightweight design and fast connection speeds.
- Quantum-Resistant Cryptography:With the advancement of quantum computing, existing encryption methods may become vulnerable. VPN providers are actively exploring quantum-resistant cryptography to ensure future security.
Enhanced Security Features
VPN providers are continuously enhancing their security features to keep pace with evolving threats.
- Multi-Factor Authentication (MFA):MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code.
- Zero-Trust Security:This approach assumes that no user or device can be trusted by default, requiring strict verification and access control policies.
Integration with Cloud Services
As cloud adoption continues to grow, VPNs are increasingly being integrated with cloud services.
- Cloud-Based VPNs:These VPNs are hosted in the cloud, offering scalability, flexibility, and ease of management.
- Integration with Cloud Platforms:VPNs are being integrated with popular cloud platforms, such as AWS, Azure, and Google Cloud, providing seamless remote access to cloud resources.
Impact of Remote Work Trends
The rise of remote work is driving a significant shift in VPN usage.
- Increased Demand:The need for secure remote access has surged, leading to increased demand for VPNs.
- Focus on User Experience:VPN providers are focusing on improving user experience, making VPNs easier to use and manage for remote workers.
Conclusive Thoughts
Remote access VPNs are powerful tools that offer a range of benefits for individuals and businesses. Whether you’re a freelancer working from home, a traveler accessing your company network, or a business needing to secure sensitive data, a remote access VPN can provide the necessary security and access you need.
Understanding the basics of how these networks work can empower you to make informed decisions about your online security and privacy.