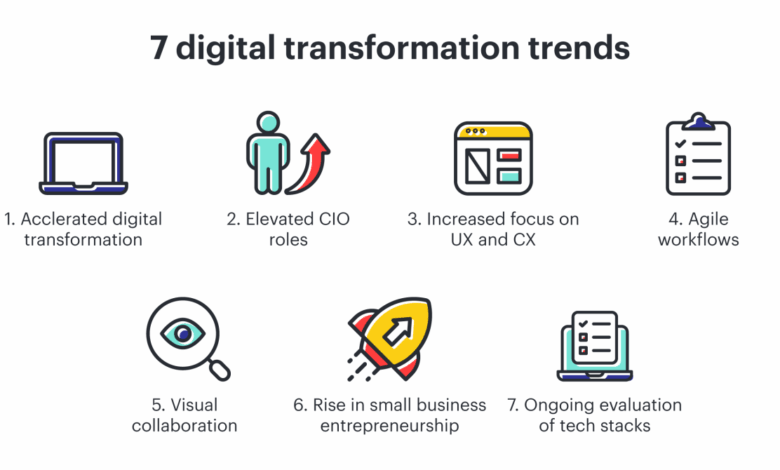
7 Digital Transformation Trends to Watch
7 Digital Transformation Trends to Watch – the world is changing faster than ever, and businesses need to adapt to stay ahead of the curve. From the rise of hyperautomation to the power of the metaverse, digital transformation is reshaping industries and creating new opportunities.
But what are the key trends that businesses need to be aware of? This article will explore seven digital transformation trends that are set to have a major impact in the coming years.
These trends are not just buzzwords; they represent fundamental shifts in the way we live, work, and interact with the world. Understanding these trends is essential for any business that wants to thrive in the digital age. Get ready to delve into a future where technology is not just a tool, but a catalyst for innovation and growth.
The Rise of Hyperautomation
Hyperautomation is transforming the way businesses operate by automating complex processes end-to-end, from data capture to decision-making. It involves a combination of advanced technologies like artificial intelligence (AI), machine learning (ML), robotic process automation (RPA), and intelligent document processing (IDP) to streamline operations, reduce errors, and boost efficiency.
The Role of AI and Machine Learning in Hyperautomation
AI and ML play a crucial role in hyperautomation by enabling intelligent decision-making and continuous improvement. AI algorithms can analyze vast amounts of data, identify patterns, and predict outcomes, while ML algorithms can learn from past experiences and adapt to changing conditions.
It’s fascinating to see how technology is shaping our world, from the rise of AI to the increasing importance of cybersecurity. But amidst these exciting developments, we’re also confronted with unsettling realities like the recent attack on a Columbia graduate student in Manhattan, as reported in this article.
This incident underscores the need for us to not only embrace technological advancements but also address the societal issues they can exacerbate, ensuring a future where technology serves humanity, not the other way around.
These technologies empower hyperautomation systems to:
- Automate complex tasks: AI and ML can handle tasks that require human judgment and reasoning, such as data analysis, risk assessment, and decision-making.
- Optimize processes: By analyzing data and identifying bottlenecks, AI and ML can help businesses optimize processes, reduce waste, and improve efficiency.
- Improve accuracy and consistency: AI and ML algorithms can perform tasks with greater accuracy and consistency than humans, reducing errors and ensuring reliable results.
- Enable self-learning and adaptation: ML algorithms can continuously learn from new data and adapt to changing conditions, ensuring that hyperautomation systems remain relevant and effective.
The Power of the Edge

The world is becoming increasingly interconnected, with devices and sensors generating vast amounts of data. Traditional cloud computing, while powerful, can struggle to handle the real-time processing demands of this data explosion. Enter edge computing, a transformative technology that brings processing power closer to the source of data, unlocking new possibilities for efficiency, responsiveness, and innovation.
From AI-powered personalization to the rise of the metaverse, there’s a lot to keep track of in the world of digital transformation. One trend that’s hard to ignore is the explosion of e-commerce, fueled by platforms like Shopify, which reports its merchants have created nearly 5 million jobs.
This kind of growth highlights the power of digital transformation to create opportunities and reshape entire industries, making it even more crucial to stay informed about the latest trends and their potential impact.
Edge Computing: A Decentralized Approach
Edge computing involves processing data at the edge of the network, closer to where it is generated, rather than relying solely on centralized cloud data centers. This distributed approach offers several advantages:
- Reduced Latency:By processing data locally, edge computing minimizes the time it takes to analyze and act upon information. This is crucial for applications requiring real-time responses, such as autonomous vehicles, industrial automation, and remote healthcare.
- Enhanced Bandwidth Efficiency:Edge computing reduces the amount of data that needs to be transmitted to the cloud, freeing up bandwidth and reducing network congestion. This is particularly beneficial in areas with limited network infrastructure or high data volumes.
- Improved Security:Edge computing can enhance data security by keeping sensitive information closer to its source, reducing the risk of data breaches during transmission.
- Increased Resilience:By distributing processing power, edge computing makes systems more resilient to outages or disruptions. If one edge node fails, others can continue to operate, ensuring business continuity.
Edge Computing and Real-Time Decision-Making
Edge computing empowers real-time decision-making by enabling rapid data analysis and response. This is particularly relevant in scenarios where time is of the essence:
- Smart Manufacturing:Edge computing allows manufacturers to monitor production lines in real-time, identify anomalies, and make adjustments to optimize efficiency and quality.
- Autonomous Vehicles:Self-driving cars rely on edge computing to process sensor data, make decisions, and navigate complex environments in real-time.
- Smart Cities:Edge computing supports intelligent traffic management systems, smart lighting, and environmental monitoring, improving city infrastructure and citizen well-being.
Examples of Edge Computing in Action
Edge computing is already making a tangible impact across various industries:
- Retail:Retailers are using edge computing to analyze customer behavior in real-time, personalize promotions, and optimize inventory management.
- Healthcare:Edge computing enables remote patient monitoring, real-time diagnostic support, and faster emergency response, improving healthcare accessibility and outcomes.
- Energy:Edge computing is used in smart grids to monitor energy consumption, optimize power distribution, and enhance grid stability.
The Impact of the Metaverse: 7 Digital Transformation Trends To Watch
The metaverse, a collective term for immersive, shared digital environments, is poised to revolutionize how we work, play, and interact. This transformative technology is not just a gaming trend; it’s a rapidly evolving landscape with the potential to reshape entire industries and redefine customer experiences.
The Metaverse’s Potential to Transform Industries
The metaverse has the potential to transform various industries, including:
- Retail:Virtual storefronts and immersive shopping experiences allow customers to try on clothes, explore products, and interact with brands in entirely new ways. For example, Nike has launched Nikeland, a virtual world within Roblox where users can customize avatars, participate in games, and purchase virtual Nike apparel.
- Education:Virtual classrooms and immersive learning environments offer personalized and interactive learning experiences, making education more engaging and accessible. Companies like Google are developing platforms that enable students to learn through virtual field trips and interactive simulations.
- Healthcare:The metaverse enables remote consultations, virtual surgeries, and medical training simulations, improving patient care and accessibility. For instance, surgeons can practice complex procedures in virtual environments before performing them on real patients.
- Manufacturing:Virtual factories and collaborative design spaces facilitate remote collaboration and streamline product development processes. Companies can use the metaverse to test prototypes, optimize production lines, and train employees in virtual environments.
- Entertainment:The metaverse is transforming entertainment with immersive concerts, virtual theme parks, and interactive games. Platforms like Decentraland and Sandbox offer users the opportunity to attend virtual events, create their own experiences, and interact with others in a shared digital space.
From AI-powered automation to the metaverse, the digital landscape is shifting rapidly. It’s important to stay ahead of the curve and understand the latest trends, like the rise of personalized experiences and the increasing reliance on data security. But beyond these broader trends, we also need to consider the impact of major societal shifts on the digital world, such as the recent overturning of Roe v.
Wade, which raises serious concerns about the safety of period tracking apps in the US. This article explores the potential risks and challenges these apps face in the new legal landscape. Understanding these issues is crucial as we navigate the evolving digital future.
The Metaverse’s Implications for Customer Experiences
The metaverse presents significant opportunities to enhance customer experiences:
- Personalized Experiences:By leveraging data and user preferences, businesses can create tailored virtual environments that cater to individual needs and interests, leading to more engaging and relevant interactions.
- Enhanced Engagement:The immersive nature of the metaverse allows customers to interact with products and services in a more meaningful way, fostering a deeper connection with brands and driving greater engagement.
- Improved Accessibility:The metaverse removes geographical barriers, making products and services accessible to a wider audience. This opens up new markets and expands customer reach.
- Enhanced Customer Service:Virtual assistants and avatars can provide personalized support and guidance within the metaverse, offering instant assistance and resolving issues efficiently.
Examples of Businesses Using the Metaverse
Several companies are already exploring the metaverse to create new opportunities:
- Meta (formerly Facebook):Meta is investing heavily in metaverse development, creating platforms like Horizon Worlds for social interaction and Horizon Workrooms for virtual collaboration.
- Microsoft:Microsoft’s Mesh platform enables users to create and experience shared virtual spaces, facilitating remote collaboration and immersive experiences.
- Epic Games:Epic Games, the creator of Fortnite, is developing a metaverse platform called Unreal Engine 5, which offers advanced graphics and interactive capabilities.
- Nvidia:Nvidia’s Omniverse platform is designed for collaborative 3D workflows, enabling teams to create and simulate complex virtual environments for various industries.
The Importance of Data Security
In today’s digital age, data is more valuable than ever before. Businesses rely on data to make decisions, improve their operations, and connect with customers. However, this reliance on data also makes it a prime target for cybercriminals. Data breaches are becoming increasingly common, and the consequences can be devastating.
Organizations of all sizes need to prioritize data security to protect themselves from these threats. This means implementing robust security measures to safeguard sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction.
Latest Threats to Data Security, 7 digital transformation trends to watch
The threat landscape for data security is constantly evolving. Here are some of the latest threats that organizations need to be aware of:
- Ransomware attacksare a major threat to data security. In a ransomware attack, cybercriminals encrypt an organization’s data and demand payment to decrypt it. Ransomware attacks have become increasingly sophisticated, and they can cripple businesses. For example, in 2021, the Colonial Pipeline ransomware attack caused widespread fuel shortages in the United States.
- Phishing attacksare a common way for cybercriminals to gain access to sensitive information. Phishing attacks involve sending emails or text messages that appear to be from a legitimate source, but are actually designed to trick recipients into clicking on malicious links or providing their login credentials.
For example, a recent phishing attack targeted users of a popular email service, and it resulted in the theft of millions of dollars.
- Data breachescan occur through a variety of methods, including hacking, malware, and insider threats. A data breach occurs when sensitive information is accessed or stolen by unauthorized individuals. For example, in 2017, a data breach at Equifax, a credit reporting agency, exposed the personal information of millions of people.
- Zero-day exploitsare vulnerabilities in software that are unknown to the vendor. These vulnerabilities can be exploited by cybercriminals to gain access to systems or data. For example, in 2021, a zero-day exploit was used to target Microsoft Exchange servers, and it resulted in the theft of sensitive data from thousands of organizations.
Mitigating Data Security Threats
Organizations can mitigate data security threats by implementing a comprehensive security strategy that includes the following measures:
- Strong passwords: Encourage employees to use strong passwords that are at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
- Multi-factor authentication: This requires users to provide two or more forms of authentication, such as a password and a code sent to their phone, before they can access their accounts. This helps to prevent unauthorized access, even if a password is compromised.
- Data encryption: This involves converting data into an unreadable format that can only be accessed by authorized individuals with the appropriate decryption key. This helps to protect data from unauthorized access, even if it is stolen.
- Regular security updates: Regularly update software and operating systems to patch known vulnerabilities. This helps to prevent cybercriminals from exploiting known weaknesses.
- Security awareness training: Educate employees about data security best practices, such as how to identify phishing attacks and how to report suspicious activity.
- Incident response plan: Develop a plan for responding to data security incidents, such as a ransomware attack or a data breach. This plan should Artikel the steps that will be taken to contain the incident, mitigate the damage, and recover from the attack.
- Data loss prevention (DLP): Implement DLP tools to monitor and control the flow of sensitive data within an organization. This helps to prevent data from being accidentally or intentionally leaked.
- Security information and event management (SIEM): Use SIEM tools to collect and analyze security data from various sources, such as firewalls, intrusion detection systems, and antivirus software. This helps to identify potential threats and security incidents.
Best Practices for Protecting Sensitive Information
Here are some best practices for protecting sensitive information:
- Limit access to sensitive data: Only grant access to sensitive data to employees who need it to perform their job duties.
- Use strong access controls: Implement strong access controls to restrict access to sensitive data based on user roles and permissions.
- Encrypt data at rest and in transit: Encrypt data that is stored on servers and databases, as well as data that is being transmitted over networks.
- Regularly back up data: Regularly back up data to ensure that it can be restored in the event of a data loss incident.
- Monitor network activity: Monitor network activity for suspicious patterns that may indicate a security incident.
- Train employees on security best practices: Regularly train employees on security best practices, such as how to identify phishing attacks and how to report suspicious activity.
Last Recap
As we navigate this exciting era of digital transformation, it’s crucial to remember that these trends are not independent entities. They intertwine and influence each other, creating a complex tapestry of change. Embracing these trends with a forward-thinking approach will empower businesses to unlock new possibilities, enhance customer experiences, and drive sustainable growth.
So, keep your eyes on the horizon, stay informed, and prepare to ride the wave of digital transformation.






