
All You Need to Know About Online Security Measures
All You Need to Know About Online Security Measures: In today’s digital age, where our lives are increasingly intertwined with the internet, safeguarding our online presence has become more crucial than ever. From personal data to financial transactions, the potential risks and threats associated with online activities are constantly evolving.
This guide will delve into the essential aspects of online security, equipping you with the knowledge and tools to protect yourself in the digital realm.
We’ll explore the importance of strong passwords and authentication methods, delve into secure browsing practices, and discuss how to protect your devices from malicious attacks. Furthermore, we’ll examine the concept of online privacy and data protection, offering insights into safe online communication and strategies for mitigating cyberattacks.
By understanding these fundamental principles and implementing the best practices Artikeld here, you can navigate the digital landscape with confidence and peace of mind.
Secure Browsing and Web Security
Navigating the digital world requires vigilance, as threats to our online security are constantly evolving. Understanding the importance of secure browsing practices and implementing robust web security measures is crucial to safeguarding our personal information and protecting our devices from malicious attacks.
Using Secure Websites (HTTPS)
The “HTTPS” protocol ensures that the communication between your browser and a website is encrypted, making it difficult for attackers to intercept and steal your sensitive data.
- Look for the padlock icon in the address bar of your browser, indicating that the connection is secure.
- Ensure that the website’s URL starts with “https://” rather than “http://”.
- Avoid websites that do not use HTTPS, especially when handling financial transactions or sharing personal information.
Browser Security Settings and Extensions, All you need to know about online security measures
Modern browsers offer various security settings and extensions that can enhance your online safety.
Online security is a vital aspect of our digital lives, protecting our personal information and financial data. It’s crucial to use strong passwords, enable two-factor authentication, and be cautious about suspicious emails or links. However, sometimes the fight for our rights needs more than just secure passwords – it needs financial backing.
That’s why I was struck by the article titled ” Will the Pro-Abortion Rights Billionaires Please Stand Up? ” – it highlights the importance of wealthy individuals stepping up to support important causes. While securing our online accounts is essential, we also need to consider how our resources can be used to fight for our rights and create a more just world.
- Enable automatic updates for your browser to ensure you have the latest security patches.
- Configure your browser’s security settings to block pop-ups, cookies, and other potentially harmful content.
- Install reputable security extensions that provide real-time threat detection, phishing protection, and password management.
Common Web-Based Threats and How to Avoid Them
It’s important to be aware of common web-based threats and implement strategies to mitigate the risks.
- Phishing Attacks: Phishing emails or websites attempt to trick you into revealing sensitive information by impersonating legitimate entities. Avoid clicking on suspicious links or providing personal details on unfamiliar websites.
- Malware: Malicious software can infect your device through downloads, malicious websites, or email attachments. Install a reputable antivirus program and keep it updated to detect and remove malware.
- Cross-Site Scripting (XSS) Attacks: XSS attacks inject malicious scripts into websites to steal user data or manipulate website behavior. Be cautious about clicking on links or entering information on unfamiliar websites.
- Denial-of-Service (DoS) Attacks: DoS attacks aim to overload a website with traffic, making it unavailable to legitimate users. While not directly targeting personal information, they can disrupt online services and impact your ability to access websites.
Online Privacy and Data Protection

In today’s digital age, protecting our online privacy is paramount. As we navigate the vast expanse of the internet, we leave a trail of data that can be collected, analyzed, and used in ways we may not fully understand. Understanding the concept of online privacy and how to safeguard our personal information is essential for navigating the digital world safely and securely.
Types of Data Collected Online
The internet is a treasure trove of data, and various entities collect it for different purposes. Here’s a glimpse into the types of data commonly collected online:
- Personal Information:This includes your name, address, phone number, email address, and date of birth. It’s often collected during account registration, online purchases, or form submissions.
- Browsing History:Websites track your browsing activities, including the pages you visit, the links you click, and the time spent on each site. This information is used for targeted advertising and website analytics.
- Location Data:Many websites and apps collect your location data, either through GPS or your IP address. This data is used for location-based services, personalized advertising, and other purposes.
- Social Media Activity:Social media platforms collect vast amounts of data about your online interactions, including your posts, likes, comments, and connections. This data is used for targeted advertising, social analytics, and to understand user behavior.
- Device Information:Websites and apps collect information about your device, such as your operating system, browser type, and device ID. This data is used for website optimization, device-specific advertising, and other purposes.
Data Usage and Its Implications
The data collected online is used for various purposes, including:
- Targeted Advertising:Companies use your browsing history, location data, and other information to tailor advertisements to your interests. This can be beneficial, providing you with relevant products and services, but it can also be intrusive and lead to privacy concerns.
- Website Analytics:Websites use data to understand user behavior and improve their services. This includes analyzing website traffic, identifying popular content, and optimizing user experience.
- Personalization:Websites and apps use data to personalize your experience, such as recommending products or services based on your past purchases or browsing history.
- Research and Development:Data is used for research and development purposes, such as understanding user trends, developing new products, and improving existing services.
- Security and Fraud Prevention:Data is used to identify and prevent fraudulent activities, such as unauthorized access to accounts or credit card fraud.
Protecting Your Personal Information
Taking proactive steps to protect your online privacy is essential. Here are some tips to safeguard your personal information:
- Use Strong Passwords:Choose strong passwords that are unique for each account and avoid using personal information like your name or birthdate. Consider using a password manager to generate and store strong passwords securely.
- Be Cautious About Sharing Information:Think twice before sharing personal information online, especially on social media. Avoid sharing sensitive information like your address, phone number, or financial details.
- Use Privacy Settings:Take advantage of privacy settings on websites and apps to control the information you share. Limit the data you share with third-party apps and services.
- Be Aware of Phishing Scams:Be cautious of suspicious emails, messages, or websites that ask for your personal information. Don’t click on links from unknown senders and verify the authenticity of any website before providing your information.
- Use a VPN:A Virtual Private Network (VPN) encrypts your internet traffic and masks your IP address, making it harder for websites and trackers to collect your data.
- Use a Privacy-Focused Browser:Some browsers, like Brave and DuckDuckGo, prioritize privacy and minimize tracking. Consider using one of these browsers for your online activities.
- Regularly Review Your Privacy Settings:Check your privacy settings on all your accounts and websites regularly to ensure they are still aligned with your privacy preferences.
Safe Online Communication: All You Need To Know About Online Security Measures
The internet has revolutionized communication, connecting people across continents and facilitating instant exchange of information. However, this ease of communication comes with inherent risks, particularly when it comes to sharing personal information. It’s crucial to understand these risks and adopt safe practices to protect your privacy and security.
Risks of Sharing Personal Information Online
Sharing personal information online can expose you to various risks, including identity theft, scams, and harassment. It’s important to be mindful of the information you disclose and to whom.
Keeping your online data secure is paramount, especially in today’s digital age. Strong passwords, multi-factor authentication, and regular software updates are just the beginning. If you’re looking for ways to improve your professional life, you might want to explore the benefits of workplace monogamy, as discussed in this insightful article: 3 benefits of workplace monogamy and how to find it.
And remember, always be cautious about sharing sensitive information online, and stay informed about the latest security threats to protect yourself from cyberattacks.
- Identity Theft:Sharing sensitive information like your Social Security number, credit card details, or birthdate online can make you vulnerable to identity theft. Criminals can use this information to open credit cards in your name, access your bank accounts, or even commit other crimes using your identity.
- Scams:Scammers often target individuals online by sending phishing emails, creating fake websites, or using social media to deceive people into revealing personal information. This information can be used to steal money, access your accounts, or compromise your devices.
- Harassment:Sharing personal information online can make you susceptible to harassment and stalking. Individuals with malicious intent can use your information to contact you, send unwanted messages, or track your online activity.
Safe Communication on Social Media and Messaging Platforms
Safe online communication requires a conscious effort to protect your privacy and avoid potential risks. Here are some guidelines for safe communication on social media and messaging platforms:
- Be Mindful of What You Share:Avoid sharing sensitive information like your home address, phone number, or financial details on public platforms. This information can be easily accessed by strangers and used for malicious purposes.
- Use Strong Passwords:Choose strong, unique passwords for all your online accounts. A strong password includes a combination of uppercase and lowercase letters, numbers, and symbols. Avoid using personal information like your name or birthday in your passwords.
- Enable Two-Factor Authentication:Two-factor authentication adds an extra layer of security to your accounts by requiring you to enter a code sent to your phone or email in addition to your password. This makes it much harder for unauthorized individuals to access your accounts.
- Be Wary of Strangers:Be cautious about interacting with strangers online. Avoid sharing personal information with individuals you don’t know and be wary of requests for financial assistance or sensitive details.
- Review Privacy Settings:Familiarize yourself with the privacy settings on social media platforms and messaging apps. Adjust your settings to control who can see your information, posts, and messages.
- Report Suspicious Activity:If you encounter suspicious activity or receive messages that make you uncomfortable, report it to the platform’s administrators.
Phishing Scams and How to Avoid Them
Phishing scams are a common form of online fraud where criminals attempt to deceive you into revealing personal information. They often use emails, text messages, or websites that appear legitimate but are actually designed to steal your data.
Keeping your online activity safe is crucial, especially in this age of data breaches and cybercrime. While you’re strengthening your passwords and using multi-factor authentication, it’s also interesting to see how businesses are investing in the future. For example, premium whiskey producer Uncle Nearest invests 5 million in BIPOC-led non-alcoholic company Hella Cocktail through their venture arm , showcasing a commitment to diversity and innovation.
These types of investments highlight the importance of staying informed about both security measures and emerging trends in the business world.
- Recognize the Signs:Phishing emails often have poor grammar, spelling errors, or unusual formatting. They may also include links to websites that look similar to legitimate ones but are actually fake.
- Don’t Click on Suspicious Links:If you receive an email or text message with a link you’re unsure about, don’t click on it. Hover your mouse over the link to see the actual URL and avoid clicking if it looks suspicious.
- Verify Requests:If you receive a request for personal information, such as your password or credit card details, from a company or organization you’re not familiar with, verify the request before providing any information. Contact the company directly using their official website or phone number to confirm the legitimacy of the request.
- Be Cautious of Urgent Requests:Scammers often use urgency as a tactic to pressure you into acting quickly. If a request seems urgent or threatening, take your time to investigate before taking any action.
- Keep Your Software Updated:Keep your operating system, web browser, and antivirus software updated to protect your device from malware and phishing attacks.
Protecting Against Cyberattacks
In today’s digital age, cyberattacks are an increasingly common threat. It’s essential to understand the various types of attacks, how to recognize them, and how to protect yourself from becoming a victim.
Common Types of Cyberattacks
Cyberattacks can take many forms, each with its own unique methods and goals. Here are some of the most prevalent types:
- Malware: This encompasses a broad category of malicious software designed to harm your device or steal your data. Examples include viruses, worms, trojans, and spyware.
- Ransomware: This type of malware encrypts your files, making them inaccessible until you pay a ransom to the attacker.
- Phishing: This involves deceiving users into revealing sensitive information like passwords or credit card details through fraudulent emails, websites, or text messages.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm a server or network with traffic, making it unavailable to legitimate users.
- Social Engineering: This technique relies on manipulating people to gain access to confidential information or systems. Attackers might impersonate trusted individuals or organizations to gain your trust.
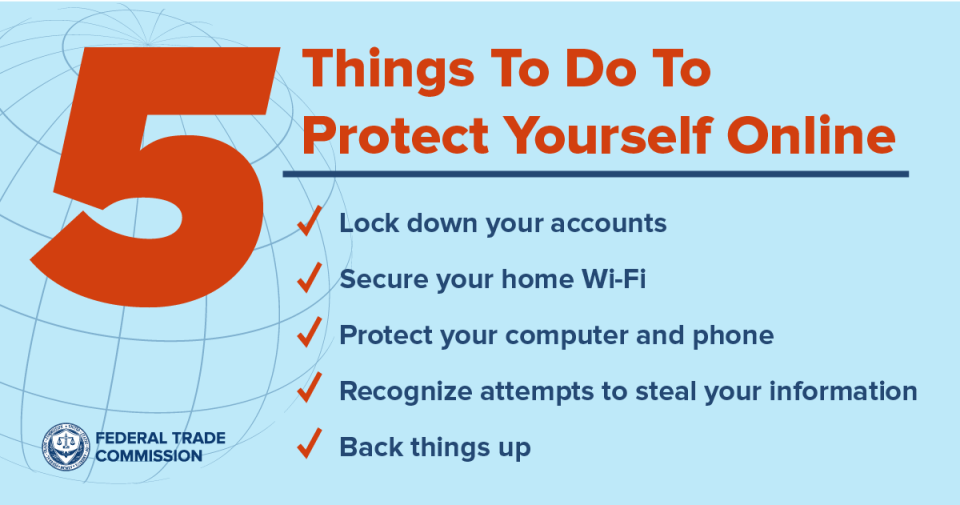
Online Security Best Practices

Online security is an ongoing process that requires constant vigilance and adaptation. While implementing various security measures is crucial, understanding and adhering to best practices can significantly enhance your online safety and protect your data.
Importance of Strong Passwords
Strong passwords are the first line of defense against unauthorized access to your online accounts.
- Use a combination of uppercase and lowercase letters, numbers, and symbols.
- Avoid using common words or personal information.
- Create unique passwords for each account.
- Use a password manager to store and generate strong passwords.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring you to provide two forms of identification before granting access to your accounts.
- After entering your password, you’ll receive a one-time code via SMS, email, or an authenticator app.
- This makes it significantly harder for attackers to gain access even if they have your password.
- Enable 2FA for all your important accounts, including email, banking, and social media.
Regular Software Updates
Software updates often include security patches that fix vulnerabilities that could be exploited by attackers.
- Keep your operating system, web browser, and all other software up to date.
- Enable automatic updates whenever possible to ensure you’re always protected.
Be Cautious of Phishing Attempts
Phishing is a common tactic used by attackers to trick you into revealing sensitive information.
- Be wary of suspicious emails, links, or messages that request personal information.
- Verify the sender’s identity before clicking on any links or opening attachments.
- Never provide personal information, such as your password or credit card details, unless you’re on a secure website.
Secure Your Wi-Fi Network
Public Wi-Fi networks are often vulnerable to eavesdropping and hacking.
- Use a strong password for your home Wi-Fi network and change it regularly.
- Avoid using public Wi-Fi for sensitive tasks like online banking or shopping.
- Consider using a VPN (Virtual Private Network) to encrypt your internet traffic when using public Wi-Fi.
Use Antivirus and Anti-Malware Software
Antivirus and anti-malware software can help protect your computer from viruses, malware, and other threats.
- Install reputable antivirus software and keep it updated.
- Scan your computer regularly for malware.
- Be cautious about downloading files from untrusted sources.
Be Aware of Social Engineering
Social engineering is a technique used by attackers to manipulate people into revealing sensitive information.
- Be wary of unsolicited requests for personal information, even from people you know.
- Never click on links or open attachments from unknown senders.
- If something seems too good to be true, it probably is.
Back Up Your Data
Regularly backing up your data can help you recover from data loss due to a cyberattack, hardware failure, or other unforeseen events.
- Use a cloud backup service or external hard drive to store copies of your important files.
- Back up your data regularly, ideally on a daily or weekly basis.
Table of Security Measures and Benefits
| Security Measure | Benefits |
|---|---|
| Strong Passwords | Protects accounts from unauthorized access |
| Two-Factor Authentication | Adds an extra layer of security, making it harder for attackers to gain access |
| Regular Software Updates | Fixes vulnerabilities that could be exploited by attackers |
| Antivirus and Anti-Malware Software | Protects against viruses, malware, and other threats |
| Secure Wi-Fi Network | Prevents unauthorized access to your network and data |
| Data Backup | Allows for data recovery in case of data loss |
Closing Summary
Staying safe online requires a proactive approach, and this guide has provided you with a comprehensive framework for achieving that goal. By implementing the security measures discussed, you can minimize your risk of falling victim to online threats and protect your valuable data.
Remember, online security is an ongoing journey, so it’s crucial to stay informed about emerging threats and adapt your practices accordingly. By embracing these principles and staying vigilant, you can navigate the digital world with greater confidence and enjoy the benefits of online connectivity without compromising your safety and privacy.






